How to do Real World Threat Modeling
Thank you for watching the video :
How to do Real World Threat Modeling
Threat modeling is a very critical step during the SDLC. Many pen testers don't realize and importance of it and don't scope the pentest accordingly. There are very limited security professionals who know how to do the threat model.
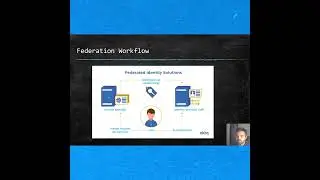
In this episode, we will threat model the online system and its authentication scheme. We will discuss the threats and trust boundaries.
ABOUT OUR CHANNEL📜
Cyber Security is a non-profit initiative taken by security professionals. Here we are uploading a series of videos to learn and get expertise in various domains of security. We are teaching tools, techniques, and methods which can be used on penetration testing assignments.
📌CHECK OUT OUR OTHER VIDEOS
▶️TOR Censorship Bypass Using VPN | CyberSecurityTV
• TOR Censorship Bypass Using VPN | Cyb...
▶️TOR Bypasses Censorship Using Bridges | CyberSecurityTV
• TOR Bypasses Censorship Using Bridges...
▶️Bypass Internet Censorship Using Tor | CyberSecurityTV
• Bypass Internet Censorship Using TOR ...
▶️Privacy and Anonymity of the Internet | How to access dark web services
• Privacy and Anonymity of the Internet...
FOLLOW US ON SOCIAL
▶️Security Blog
https://bhaumikshah04.blogspot.com/
▶️Facebook
/ infosecforstarters
#CyberSecurityTV
#darkweb
#PrivacyandAnonymity
CyberSecurityTV
Related Searches:
threat modeling tools
microsoft threat model
web application threat model example
threat modeling certification
Watch video How to do Real World Threat Modeling online, duration hours minute second in high quality that is uploaded to the channel CyberSecurityTV 21 February 2022. Share the link to the video on social media so that your subscribers and friends will also watch this video. This video clip has been viewed 38,921 times and liked it 731 visitors.