What are OAuth Security Vulnerabilities | CybersecurityTv
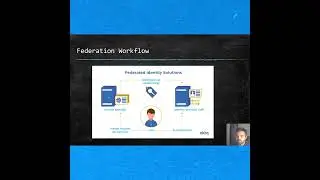
OAuth is a standard mechanism that we use every day. There are some security flaws in the workflow if not implemented correctly.
In this episode, I will teach you what is OAuth workflow, how does it work, how you can find out if the application is using OAuth, and some common vulnerabilities to spot.
Join our Facebook page: / infosecforstarters
🍁 𝐀𝐁𝐎𝐔𝐓 𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 🍁
Cyber Security is an initiative taken by security professionals. Here we are uploading a series of videos to learn and get expertise in various domains of security. We are teaching tools, techniques, and methods which can be used on penetration testing assignments.
✨ 𝗝𝗢𝗜𝗡 𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 ✨
➟ CyberSecurityTV Channel: / @cybersecuritytv
💌 𝐋𝐄𝐓'𝐒 𝐒𝐓𝐀𝐘 𝐈𝐍 𝐓𝐎𝐔𝐂𝐇 💌
➟ Security Blog
https://bhaumikshah04.blogspot.com/
➟ Facebook
/ infosecforstarters
📌𝐑𝐄𝐅𝐄𝐑𝐍𝐂𝐄𝐒
https://vpnoverview.com/privacy/anony...
https://proton.me/mail/security
📌𝐂𝐲𝐛𝐞𝐫𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲𝐓𝐕 𝐎𝐓𝐇𝐄𝐑 𝐕𝐈𝐃𝐄𝐎𝐒
➟Dark Web Chat | Pidgin IM | Shorts
🔗 • Dark Web Chat | Pidgin IM | Shorts
➟Guardio Review - Top Rated Security Extension | CyberSecurityTV
🔗 • Guardio Review | Top Rated Security E...
➟ How to Setup Pidgin | Dark Web Chat
🔗 • How to Setup Pidgin | Dark Web Chat |...
➟ What are Dark Web | Email Providers | CyberSecurityTv
🔗 • What are Dark Web | Email Providers |...
#webapppentest #appsec #applicationsecurity #apitesting #apipentest #cybersecurityonlinetraining #freesecuritytraining #penetrationtest #ethicalhacking #burpsuite #pentestforbegineers #security professionals
𝐑𝐄𝐋𝐀𝐓𝗘𝐃 𝐒𝐄𝐀𝐑𝐂𝐇𝐄𝐒:
OAuth security best practices
OAuth vulnerabilities Medium
OAuth Pentesting Checklist
OAuth attacks
Watch video What are OAuth Security Vulnerabilities | CybersecurityTv online, duration hours minute second in high quality that is uploaded to the channel CyberSecurityTV 08 May 2023. Share the link to the video on social media so that your subscribers and friends will also watch this video. This video clip has been viewed 13,478 times and liked it 119 visitors.




![¡COMO PESCAR el KRAKEN en [FISCH] [ROBLOX]! 😱](https://images.reviewsvideo.ru/videos/1buj1B7h2BI)