Roy Hopkins: Establishing root seeds in a vTPM with COCONUT-SVSM in Confidential VM Remote
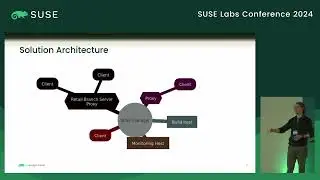
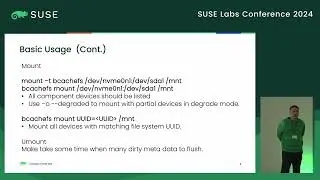
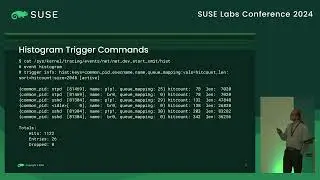
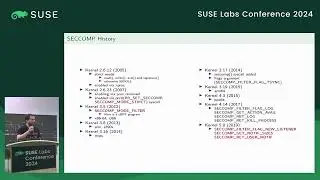
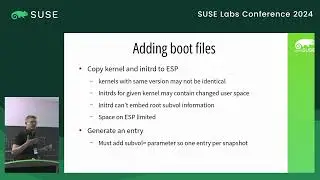
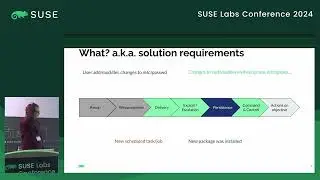
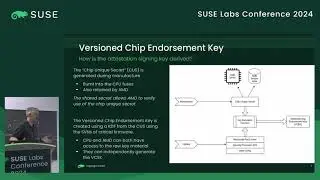
Confidential Computing for virtual machines provides hardware protection for data as it is being processed on an untrusted host, giving strong assurance that the guest memory and context is protected from observation and manipulation by the host. In order to ensure integrity of the workload deployed into a confidential VM, CPU vendors include the ability to remotely attest the startup state of the guest. This provides verifiable cryptographic evidence that the guest is running inside a patched, up-to-date CC environment and confirms exactly what firmware the guest is running. In order to retain integrity from the verified firmware, unlock an encrypted disk and boot the operating system, a traditional secure boot process can be used. However, a TPM or equivalent is required to implement secure boot. COCONUT-SVSM provides a secure environment to implement a virtual TPM where keys and state are protected both from the host and the guest firmware. Manufacturing a vTPM requires access to persistent root seeds that must remain secure and available even when the guest is migrated to a different host. This talk introduces the process and capabilities of remote attestation with AMD SEV-SNP and discusses how this can be used during the the initialisation of COCONUT-SVSM to securely obtain vTPM seeds from a key broker service.
Watch video Roy Hopkins: Establishing root seeds in a vTPM with COCONUT-SVSM in Confidential VM Remote online, duration hours minute second in high quality that is uploaded to the channel SUSE Labs 10 June 2024. Share the link to the video on social media so that your subscribers and friends will also watch this video. This video clip has been viewed 99 times and liked it 3 visitors.