PHP SQL Injection Example
Key Moments
00:00 - Intro
00:08 - SQL Injection
01:18 - Insecure Code Review
02:28 - Testing Prepared Statement Code
03:33 - Prepared Statement Code Review
05:07 - Conclusion
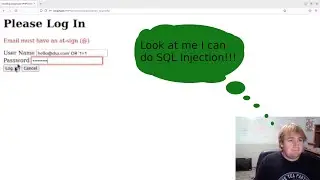
In this tutorial I quickly show an example of how to execute an SQL injection attack on a PHP website not using prepared statements.
I then change the code to use a prepared statement (a SELECT query in particular) using the mysqli library. The functions used in the code are execute(), bind_param(), prepare(), and bind_result().
The order to call them is:
prepare()
bind_param()
execute()
bind_result()
Of course the above order is missing all the variables and such but you can go to my GitHub repo, https://github.com/PhysicsUofRAUI/PHP..., to see the code in full.
At the moment the 'unsecure' branch does not use prepared statements and the 'main' branch uses prepared statements but still has plain text passwords.
The next video in this series will be showing how to use hashed passwords.
If you do have a website that has this vulnerability feel free to contact me, and I can take a look for you. My email is [email protected].
Watch video PHP SQL Injection Example online, duration hours minute second in high quality that is uploaded to the channel Kody Rogers 11 October 2022. Share the link to the video on social media so that your subscribers and friends will also watch this video. This video clip has been viewed 1,009 times and liked it 5 visitors.